“The upgrade of traditional governance thinking is urgent, it must keep up with the data generation methods and exchange requirements.”
Editor’s note: This article comes from the WeChat public account ” Cloud Rider “(ID: tenyun700) , author: hackers eagle Internet security experts, IDF laboratory founder.

The new crown epidemic has accelerated the arrival of human online life, but it is difficult to quickly increase the trust relationship between humans and technology. Concerns about data privacy are still prevalent in front of “anti-epidemic technologies” such as contact tracing.
The core question is, in the era of digital governance, how to reinterpret the key concepts of trust, privacy, and social governance?
A month ago, Apple and Google announced the joint development of a contact tracking system to meet the challenge of the new crown epidemic.
This system will use the existing Bluetooth technology to track the distance between different mobile phones-if a user ’s new coronary pneumonia virus test is positive, then other users ’mobile phones will search for data in the past to determine whether there is The risk of prolonged contact with infected persons.
The plan may cover about one-third of the world ’s population. Although the two companies emphasized that this system can protect user privacy, many people remain cautious.
The data also proves this. The latest survey by Pew Labs shows that 62% of people said they were unacceptable when asked how they would use smartphones to understand their personal social isolation.
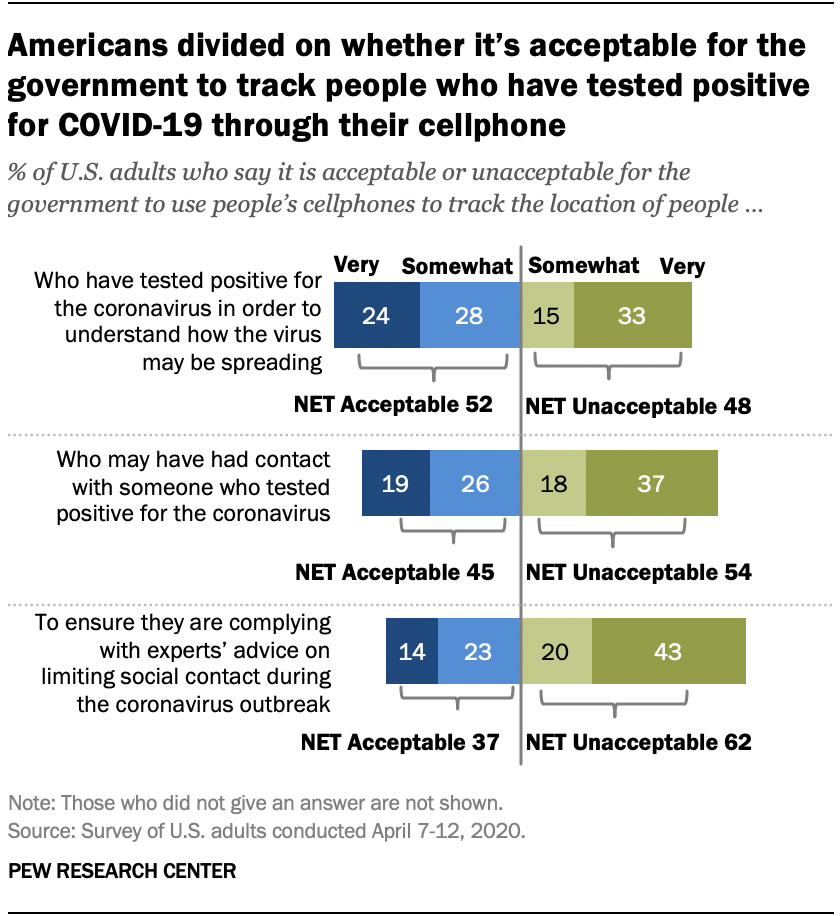
Epidemiology experts point out that unless the download rate of contact tracking apps reaches more than 60% of the population in a specific area, the speed of tracking viruses can exceed the speed of virus transmission.
That is to say, if there is no trust, no matter how advanced the contact tracking technology is, its “magic” cannot be exerted.
This reflects the widespread “trust” crisis facing the development of science and technology today. The epidemic has accelerated the arrival of a “contactless society”, but it has failed to increase the level of trust between humans and technology in the short term. ThisBehind the problem is a reinterpretation of concepts such as privacy, trust, and social governance.
When all industries in the world are undergoing digital transformation, and when the more general digital life comes ahead of time under the acceleration of the epidemic, the concepts of privacy and trust in the traditional physical space are facing challenges and urgent changes are needed-
Change itself does not mean “death”, but represents “evolution”.
01 Trust Transformation: From ” “Traditional trust” to “Digital trust”
The “Matrix” released in 1999 is both a “Buddhist Apocalypse” and an “Einstein-Rosen Bridge” wormhole for insight into the physical universe and the digital universe.
“The damage caused in the digital universe will become physical damage.” It now appears that this prediction is not alarmist-
In the past, cybersecurity incidents were only destroyed by data with a controllable scale and the resulting local “services are unavailable”; today ’s cybersecurity incidents have been subject to extortion of digital assets and large-scale services Shut down. In the foreseeable future, the harm caused by cybersecurity incidents will be closely related to human life and health-especially in the coming era of Internet of Everything.
The upgrading of traditional governance thinking is an urgent task. It must keep up with the data generation methods and exchange requirements.
In the traditional thinking of governance, we are continually “building dams” to resist floods. And when we face the ocean and the sea today, it is better to let the data “safely flow” and integrate security into the flow instead of “high-level deterrence”: The question is, how to balance security while ensuring data mobility?
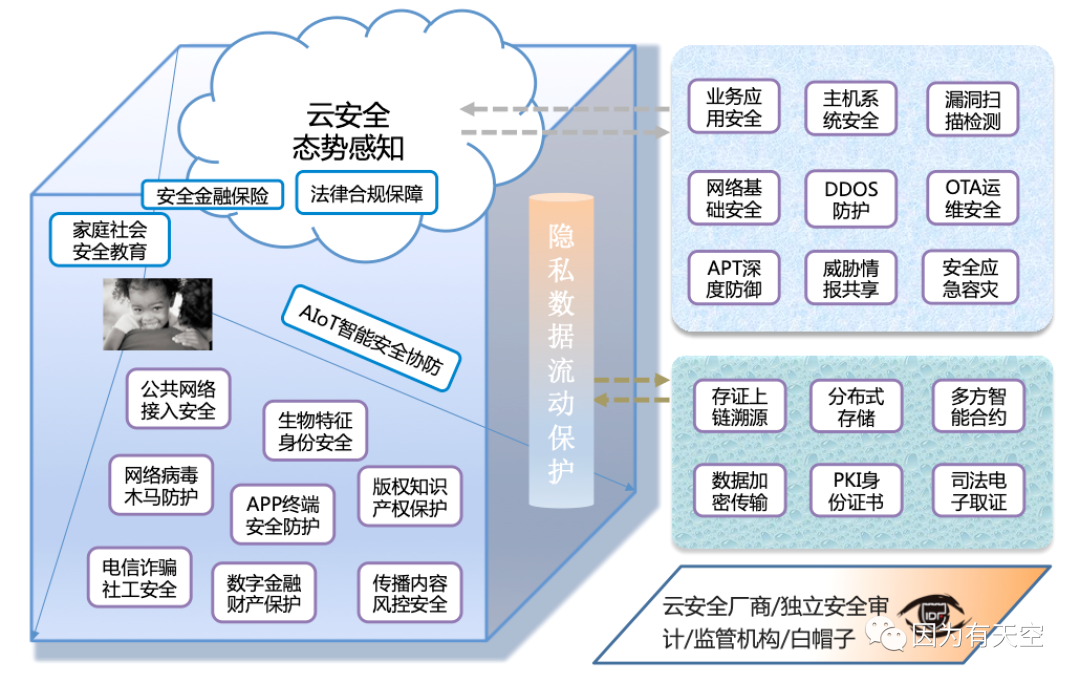 Figure: Cloud + private data protection three-body cube. As the spatial and temporal distance of data flow becomes more and more multidimensional and discrete, our privacy data protection is like a cube containing three body spaces (three spaces with multiple threats, security and resilience, and data flow). The overall trend is: clouding of security services, chaining of data encryption, and symbiosis of service provision. Source: IDF Lab
Figure: Cloud + private data protection three-body cube. As the spatial and temporal distance of data flow becomes more and more multidimensional and discrete, our privacy data protection is like a cube containing three body spaces (three spaces with multiple threats, security and resilience, and data flow). The overall trend is: clouding of security services, chaining of data encryption, and symbiosis of service provision. Source: IDF Lab
The basis for the upgrading of social governance thinking is actually the transition from “traditional trust” to “digital trust”.
Wharton professor Kevin Werbach once described four “universal trust architectures”:
-
Point-to-point trust: that is, trust between people;
-
Leviathan trust: a large number of contracts / contract systems appear, because mutual trust between the government and the state will help resolve disputes, and parties that do not trust each other can reach agreement through the contract;
-
Intermediary trust: This kind of trust is like a credit card system. Even if there is no trust relationship, buyers and sellers can still use the third-party credit system for business transactions;
-
Distributed trust: Emerging digital trust in specific security systems such as blockchain that attempts to de-intermediate.
The fourth kind of trust “digital trust” he mentioned inherits the traditional definition and expression of trust in trust. It transforms traditional trust in legal compliance, ethical and moral experience in the form of words, and state machine into trust in a program composed of code encryption and algorithms based on mathematical and physical rules.
Trust at this time refers to the confidence in the secure digital world established by people, processes and technology, and the confidence of the country and individuals, businesses and consumers in the ability to protect data and personal privacy.
In the future, for those countries and enterprises that can win trust, “digital trust” may become a measurable value-like gold-like “credit commodity”, and reconstruct the future society together with digital currency Economic model. At the same time, it may break through the weaknesses of human nature, the limitations of individuals and the asymmetry of culture in order to achieve capabilities that would otherwise be impossible.
It sounds like a little too “idealistic”: is it possible to realize such a beautiful idea?
At the technical level, “Zero Trust Network” (or “Zero Trust” for short) provides a practical idea. It can replace the limited trust of previous layers of defense, and overcome the privacy compliance barriers of digital trust.
02 “Digital Trust” technology implementation path: zero trust
In mid-December 2009, a large-scale cyber attack called Operation Aurora broke out. The target of this attack is more than 20 large companies, including Google, Adobe Systems, Juniper Networks, Rackspace, Yahoo, etc.
Google felt painstakingly and decided to abandon the traditional “validation and trust” system security protection mechanism and switch to using the “zero trust” security architecture model to carry out some of its business.
What is “zero trust”?
nowPeople have realized that the identity of users based on personal accounts has caused many privacy risks. In the open Internet world, the boundaries of countries, enterprises, individuals and terminal equipment have been broken, and the collaboration capabilities of technology companies have been unprecedentedly strong. The traditional social governance system constructed through laws and industry standards is beginning to face new challenges:
-
The complexity brought about by multiple identities and roles of natural persons;
-
The increasingly rich application iterations and acceleration of the data life cycle;
-
Comprehensive response of security services, lagging security education and shortage of security talents;
-
Depth, breadth and boundary fusion of multi-space high-speed network.
Under such a background, if we do not revise the existing network security architecture and break through the constraints of physical and logical boundary thinking, we can only see that the red and yellow security risks are spreading like a spark, causing trust crisis. (As shown below)
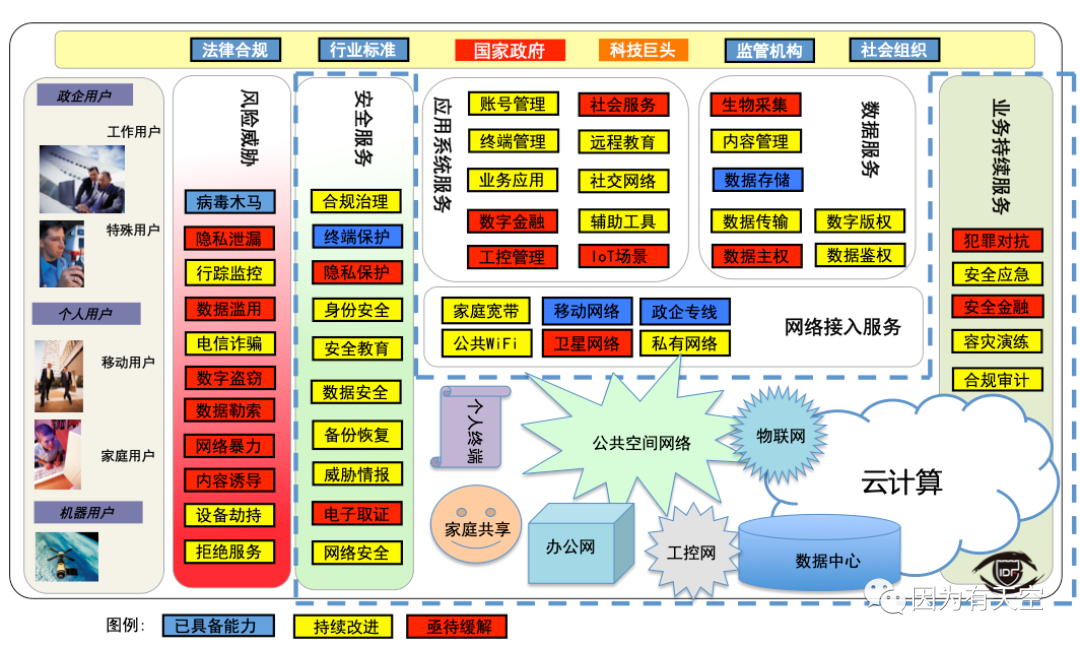
Internet governance and risk control capability assessment 2020. Source: IDF Lab
As the best network data security architecture in the future generally recognized by the Internet security industry, the mission of the “Zero Trust Network” is to protect national and corporate data and all other personal digital assets. It provides the possibility of landing for “digital trust” at the technical level.
Simply put, the strategy of “zero trust” is not to trust anyone, unless the network clearly knows the identity of the accessor, no one wants to enter.
“Zero Trust Network” is a security concept proposed by Forrester, Gartner and many other security companies in 2013. The founder is former Forrester chief analyst John Kindervag.
In Forrester ’s view, in the current data-centric world, threats not only come from the outside, many serious information security incidents are erupted inside the organization, and are derived from “we believe it is credible” User or system.
In the network under this architecture, there are no privileged users, traffic, systems, and regions, and there is no such thing as “intranet is more secure” and “extranet is insecure”In other words, the overall security of the network starts from zero.
Compared with traditional security frameworks, what is special about “zero trust”?
The “original” digital trust is built on the Internet ’s own security vulnerability, and based on the “barrel principle” of security, it has to rely on the creation of a series of security product solutions and services such as firewalls, antiviruses, and digital certificates. Third-party audits and other initiatives to maintain their trust, while generating more security complexity related issues.
This trust framework adds more intermediate links and digital rights asymmetry to the trust subject—users, forming multiple separate and separate digital rights hosting relationships based on account, identity, storage, etc., establishing digital trust is like There is no obvious certainty between the fish in the ocean and the isolated island;
The “zero trust” grants trust authority to the trust subject itself by breaking and reducing the intermediate links.
Since the user enters the network, no matter how his IP address or role changes (such as the switching of its access subject), the strong security authentication method given to him is used to simplify the practice of hierarchical authentication trust release inside and outside the network, so that users The subject is always in the safe (verification) trusted and controllable range, so as to finally achieve a face-based authentication method similar to that in the real world, thoroughly build a trust transition from the real world to the virtual world, and achieve a seamless connection between online and offline. ” Digital trust “.
In short, the practice of a zero-trust network architecture is to redefine the base of “digital trust” by completely changing the passive offensive and defensive way of network security, strengthen network resilience, and replace short-board security with long-board advantages. Determinism.

Jon Postel ’s early map of the Internet in February 1982
This architecture has subverted the paradigm of access control. It has guided the existing security architecture from “network centralization” to “identity centralization”. Its essential appeal is to use identity-centric access control. To adapt to the current network environment.
Using mature encryption technology, reshaping based on cloud computing and big data, and using artificial intelligence, machine learning, and security automation systems, the vision of a “zero trust network” can be fully realized. This ensures the “safe flow” of data.
03 “The End of the World” Never Comes
The Terminator, released in 1984, predicted that it would be August 29, 1997 at the end of the 20th century. Because the “Skynet”, an intelligent missile defense system developed by the United States, generates self-awareness, it regards all humans as a threat, launches a nuclear bomb at the Soviet Union, and activates nuclear bundling.
3 billion people died on the day, and the survivors called this day “Judgment Day.”
“Terminator 2” released in 1991 “rewrote” the future, and “Terminator 3” changed the Judgment Day to begin on July 24, 2004, predicting that by 2029, the nuclear-destructed earth will have The computer “Skynet” ruled, and humans were almost wiped out.
Science fiction works about the destruction of mankind by science and technology are not uncommon, and human beings have passed the “doomsday” of those prophecies safely again and again.
At the 2020 Winter Davos Forum, Huawei ’s founder Ren Zhengfei held a peak dialogue with historian Juvar Hullali on the relationship between humanity ’s future and technological development.
The two of them, one is a deep-minded entrepreneur and the other is a scholar who has insight into the future. This is regarded by the netizens as a “wise debate” about the future. They talked about some interesting topics and held different views from each other:
Juval Heralli said that the artificial intelligence revolution and biotechnology revolution in the 21st century will make history repeat itself. Ren Zhengfei believes that the current technological progress is not fundamentally different from the panic caused by the emergence of trains, ships and textile machinery in the past-since atomic energy can be used by people, so can artificial intelligence.
Yuwar Herali is worried about the future invasion of human body, brain and life. Ren Zhengfei said that neither China nor the United States really want to understand artificial intelligence. He believes that the so-called “invasion” will not appear in the next two to three decades or longer.
Ren Zhengfei believes that the development of technology will enhance human activity; Herald believes that technology will play two roles: at the same time, it will limit and enhance personal capabilities or initiative …

This reflects to a certain extent the two attitudes of mankind when facing the future.
Herali, his historian, looks at the evolution of social laws from a macro perspective of history. His starting point is to ask questions from past experience to the future, and his attitude is compassionate. In his eyes, humans
 Figure: Cloud + private data protection three-body cube. As the spatial and temporal distance of data flow becomes more and more multidimensional and discrete, our privacy data protection is like a cube containing three body spaces (three spaces with multiple threats, security and resilience, and data flow). The overall trend is: clouding of security services, chaining of data encryption, and symbiosis of service provision. Source: IDF Lab
Figure: Cloud + private data protection three-body cube. As the spatial and temporal distance of data flow becomes more and more multidimensional and discrete, our privacy data protection is like a cube containing three body spaces (three spaces with multiple threats, security and resilience, and data flow). The overall trend is: clouding of security services, chaining of data encryption, and symbiosis of service provision. Source: IDF Lab Point-to-point trust: that is, trust between people;
Leviathan trust: a large number of contracts / contract systems appear, because mutual trust between the government and the state will help resolve disputes, and parties that do not trust each other can reach agreement through the contract;
Intermediary trust: This kind of trust is like a credit card system. Even if there is no trust relationship, buyers and sellers can still use the third-party credit system for business transactions;
Distributed trust: Emerging digital trust in specific security systems such as blockchain that attempts to de-intermediate.
The fourth kind of trust “digital trust” he mentioned inherits the traditional definition and expression of trust in trust. It transforms traditional trust in legal compliance, ethical and moral experience in the form of words, and state machine into trust in a program composed of code encryption and algorithms based on mathematical and physical rules.
Trust at this time refers to the confidence in the secure digital world established by people, processes and technology, and the confidence of the country and individuals, businesses and consumers in the ability to protect data and personal privacy.
In the future, for those countries and enterprises that can win trust, “digital trust” may become a measurable value-like gold-like “credit commodity”, and reconstruct the future society together with digital currency Economic model. At the same time, it may break through the weaknesses of human nature, the limitations of individuals and the asymmetry of culture in order to achieve capabilities that would otherwise be impossible.
It sounds like a little too “idealistic”: is it possible to realize such a beautiful idea?
At the technical level, “Zero Trust Network” (or “Zero Trust” for short) provides a practical idea. It can replace the limited trust of previous layers of defense, and overcome the privacy compliance barriers of digital trust.
02 “Digital Trust” technology implementation path: zero trust
In mid-December 2009, a large-scale cyber attack called Operation Aurora broke out. The target of this attack is more than 20 large companies, including Google, Adobe Systems, Juniper Networks, Rackspace, Yahoo, etc.
Google felt painstakingly and decided to abandon the traditional “validation and trust” system security protection mechanism and switch to using the “zero trust” security architecture model to carry out some of its business.
What is “zero trust”?
nowPeople have realized that the identity of users based on personal accounts has caused many privacy risks. In the open Internet world, the boundaries of countries, enterprises, individuals and terminal equipment have been broken, and the collaboration capabilities of technology companies have been unprecedentedly strong. The traditional social governance system constructed through laws and industry standards is beginning to face new challenges:
-
The complexity brought about by multiple identities and roles of natural persons;
-
The increasingly rich application iterations and acceleration of the data life cycle;
-
Comprehensive response of security services, lagging security education and shortage of security talents;
-
Depth, breadth and boundary fusion of multi-space high-speed network.
Under such a background, if we do not revise the existing network security architecture and break through the constraints of physical and logical boundary thinking, we can only see that the red and yellow security risks are spreading like a spark, causing trust crisis. (As shown below)

Internet governance and risk control capability assessment 2020. Source: IDF Lab
As the best network data security architecture in the future generally recognized by the Internet security industry, the mission of the “Zero Trust Network” is to protect national and corporate data and all other personal digital assets. It provides the possibility of landing for “digital trust” at the technical level.
Simply put, the strategy of “zero trust” is not to trust anyone, unless the network clearly knows the identity of the accessor, no one wants to enter.
“Zero Trust Network” is a security concept proposed by Forrester, Gartner and many other security companies in 2013. The founder is former Forrester chief analyst John Kindervag.
In Forrester ’s view, in the current data-centric world, threats not only come from the outside, many serious information security incidents are erupted inside the organization, and are derived from “we believe it is credible” User or system.
In the network under this architecture, there are no privileged users, traffic, systems, and regions, and there is no such thing as “intranet is more secure” and “extranet is insecure”In other words, the overall security of the network starts from zero.
Compared with traditional security frameworks, what is special about “zero trust”?
The “original” digital trust is built on the Internet ’s own security vulnerability, and based on the “barrel principle” of security, it has to rely on the creation of a series of security product solutions and services such as firewalls, antiviruses, and digital certificates. Third-party audits and other initiatives to maintain their trust, while generating more security complexity related issues.
This trust framework adds more intermediate links and digital rights asymmetry to the trust subject—users, forming multiple separate and separate digital rights hosting relationships based on account, identity, storage, etc., establishing digital trust is like There is no obvious certainty between the fish in the ocean and the isolated island;
The “zero trust” grants trust authority to the trust subject itself by breaking and reducing the intermediate links.
Since the user enters the network, no matter how his IP address or role changes (such as the switching of its access subject), the strong security authentication method given to him is used to simplify the practice of hierarchical authentication trust release inside and outside the network, so that users The subject is always in the safe (verification) trusted and controllable range, so as to finally achieve a face-based authentication method similar to that in the real world, thoroughly build a trust transition from the real world to the virtual world, and achieve a seamless connection between online and offline. ” Digital trust “.
In short, the practice of a zero-trust network architecture is to redefine the base of “digital trust” by completely changing the passive offensive and defensive way of network security, strengthen network resilience, and replace short-board security with long-board advantages. Determinism.

Jon Postel ’s early map of the Internet in February 1982
This architecture has subverted the paradigm of access control. It has guided the existing security architecture from “network centralization” to “identity centralization”. Its essential appeal is to use identity-centric access control. To adapt to the current network environment.
Using mature encryption technology, reshaping based on cloud computing and big data, and using artificial intelligence, machine learning, and security automation systems, the vision of a “zero trust network” can be fully realized. This ensures the “safe flow” of data.
03 “The End of the World” Never Comes
The Terminator, released in 1984, predicted that it would be August 29, 1997 at the end of the 20th century. Because the “Skynet”, an intelligent missile defense system developed by the United States, generates self-awareness, it regards all humans as a threat, launches a nuclear bomb at the Soviet Union, and activates nuclear bundling.
3 billion people died on the day, and the survivors called this day “Judgment Day.”
“Terminator 2” released in 1991 “rewrote” the future, and “Terminator 3” changed the Judgment Day to begin on July 24, 2004, predicting that by 2029, the nuclear-destructed earth will have The computer “Skynet” ruled, and humans were almost wiped out.
Science fiction works about the destruction of mankind by science and technology are not uncommon, and human beings have passed the “doomsday” of those prophecies safely again and again.
At the 2020 Winter Davos Forum, Huawei ’s founder Ren Zhengfei held a peak dialogue with historian Juvar Hullali on the relationship between humanity ’s future and technological development.
The two of them, one is a deep-minded entrepreneur and the other is a scholar who has insight into the future. This is regarded by the netizens as a “wise debate” about the future. They talked about some interesting topics and held different views from each other:
Juval Heralli said that the artificial intelligence revolution and biotechnology revolution in the 21st century will make history repeat itself. Ren Zhengfei believes that the current technological progress is not fundamentally different from the panic caused by the emergence of trains, ships and textile machinery in the past-since atomic energy can be used by people, so can artificial intelligence.
Yuwar Herali is worried about the future invasion of human body, brain and life. Ren Zhengfei said that neither China nor the United States really want to understand artificial intelligence. He believes that the so-called “invasion” will not appear in the next two to three decades or longer.
Ren Zhengfei believes that the development of technology will enhance human activity; Herald believes that technology will play two roles: at the same time, it will limit and enhance personal capabilities or initiative …

This reflects to a certain extent the two attitudes of mankind when facing the future.
Herali, his historian, looks at the evolution of social laws from a macro perspective of history. His starting point is to ask questions from past experience to the future, and his attitude is compassionate. In his eyes, humans
The complexity brought about by multiple identities and roles of natural persons;
The increasingly rich application iterations and acceleration of the data life cycle;
Comprehensive response of security services, lagging security education and shortage of security talents;
Depth, breadth and boundary fusion of multi-space high-speed network.
Under such a background, if we do not revise the existing network security architecture and break through the constraints of physical and logical boundary thinking, we can only see that the red and yellow security risks are spreading like a spark, causing trust crisis. (As shown below)

Internet governance and risk control capability assessment 2020. Source: IDF Lab
As the best network data security architecture in the future generally recognized by the Internet security industry, the mission of the “Zero Trust Network” is to protect national and corporate data and all other personal digital assets. It provides the possibility of landing for “digital trust” at the technical level.
Simply put, the strategy of “zero trust” is not to trust anyone, unless the network clearly knows the identity of the accessor, no one wants to enter.
“Zero Trust Network” is a security concept proposed by Forrester, Gartner and many other security companies in 2013. The founder is former Forrester chief analyst John Kindervag.
In Forrester ’s view, in the current data-centric world, threats not only come from the outside, many serious information security incidents are erupted inside the organization, and are derived from “we believe it is credible” User or system.
In the network under this architecture, there are no privileged users, traffic, systems, and regions, and there is no such thing as “intranet is more secure” and “extranet is insecure”In other words, the overall security of the network starts from zero.
Compared with traditional security frameworks, what is special about “zero trust”?
The “original” digital trust is built on the Internet ’s own security vulnerability, and based on the “barrel principle” of security, it has to rely on the creation of a series of security product solutions and services such as firewalls, antiviruses, and digital certificates. Third-party audits and other initiatives to maintain their trust, while generating more security complexity related issues.
This trust framework adds more intermediate links and digital rights asymmetry to the trust subject—users, forming multiple separate and separate digital rights hosting relationships based on account, identity, storage, etc., establishing digital trust is like There is no obvious certainty between the fish in the ocean and the isolated island;
The “zero trust” grants trust authority to the trust subject itself by breaking and reducing the intermediate links.
Since the user enters the network, no matter how his IP address or role changes (such as the switching of its access subject), the strong security authentication method given to him is used to simplify the practice of hierarchical authentication trust release inside and outside the network, so that users The subject is always in the safe (verification) trusted and controllable range, so as to finally achieve a face-based authentication method similar to that in the real world, thoroughly build a trust transition from the real world to the virtual world, and achieve a seamless connection between online and offline. ” Digital trust “.
In short, the practice of a zero-trust network architecture is to redefine the base of “digital trust” by completely changing the passive offensive and defensive way of network security, strengthen network resilience, and replace short-board security with long-board advantages. Determinism.

Jon Postel ’s early map of the Internet in February 1982
This architecture has subverted the paradigm of access control. It has guided the existing security architecture from “network centralization” to “identity centralization”. Its essential appeal is to use identity-centric access control. To adapt to the current network environment.
Using mature encryption technology, reshaping based on cloud computing and big data, and using artificial intelligence, machine learning, and security automation systems, the vision of a “zero trust network” can be fully realized. This ensures the “safe flow” of data.
03 “The End of the World” Never Comes
The Terminator, released in 1984, predicted that it would be August 29, 1997 at the end of the 20th century. Because the “Skynet”, an intelligent missile defense system developed by the United States, generates self-awareness, it regards all humans as a threat, launches a nuclear bomb at the Soviet Union, and activates nuclear bundling.
3 billion people died on the day, and the survivors called this day “Judgment Day.”
“Terminator 2” released in 1991 “rewrote” the future, and “Terminator 3” changed the Judgment Day to begin on July 24, 2004, predicting that by 2029, the nuclear-destructed earth will have The computer “Skynet” ruled, and humans were almost wiped out.
Science fiction works about the destruction of mankind by science and technology are not uncommon, and human beings have passed the “doomsday” of those prophecies safely again and again.
At the 2020 Winter Davos Forum, Huawei ’s founder Ren Zhengfei held a peak dialogue with historian Juvar Hullali on the relationship between humanity ’s future and technological development.
The two of them, one is a deep-minded entrepreneur and the other is a scholar who has insight into the future. This is regarded by the netizens as a “wise debate” about the future. They talked about some interesting topics and held different views from each other:
Juval Heralli said that the artificial intelligence revolution and biotechnology revolution in the 21st century will make history repeat itself. Ren Zhengfei believes that the current technological progress is not fundamentally different from the panic caused by the emergence of trains, ships and textile machinery in the past-since atomic energy can be used by people, so can artificial intelligence.
Yuwar Herali is worried about the future invasion of human body, brain and life. Ren Zhengfei said that neither China nor the United States really want to understand artificial intelligence. He believes that the so-called “invasion” will not appear in the next two to three decades or longer.
Ren Zhengfei believes that the development of technology will enhance human activity; Herald believes that technology will play two roles: at the same time, it will limit and enhance personal capabilities or initiative …

This reflects to a certain extent the two attitudes of mankind when facing the future.
Herali, his historian, looks at the evolution of social laws from a macro perspective of history. His starting point is to ask questions from past experience to the future, and his attitude is compassionate. In his eyes, humans
