After upgrading to iOS 13, in addition to the cool features, new reminders, new Emoji expressions and other new features, many users have also found that “pop-ups” have become more and more frequent, these bombs The window will tell you how many times the authorized app has obtained your location information in the recent past, which will tell you which apps want to read Bluetooth permissions…
After the iOS 12 update last year, Apple launched a new “Privacy” website due to changes in its privacy policy. With the update of new hardware and new systems, Apple has updated its privacy page content today, including Safari, maps, photos, information, Siri, wallet, health and Apple account login. New related introductions and white papers are on the line.

How Apple Prevents Tracking and How to Track Your Apple
Location Services
As mentioned above, location service privacy protection is now more secure. When applying the location permission before, iOS will be divided into “Always Allow”, “Use Application Period” and “Never”. In iOS 13, the “Allow Once” option has been added instead of the previous “Always Allow”. , suitable for those who temporarily obtain one or two location informationuse.

In addition, iOS will also track how many times these apps have acquired your location information within a certain period of time, and give reminders through pop-up windows to prevent users from frequently obtaining location information in the background after the user misuses. Location information including Bluetooth and WiFi connected to you will be protected, and iOS 13 will further reduce the number of times the app asks to connect to Bluetooth and WiFi.

In a nutshell, location service control is now becoming more restrictive, and Apple protects your personal privacy from abuse by minimizing the need for applications to directly capture or infer where you have been.
Sign in with Apple
Another new feature, “Sign in with Apple,” will better protect your real email address. Since most of today’s applications require a mailbox or a third-party account to log in, there are a lot of privacy risks, such as spam and accurate personalized marketing. As more and more users log on to websites and applications, many people suffer. Unspeakable.
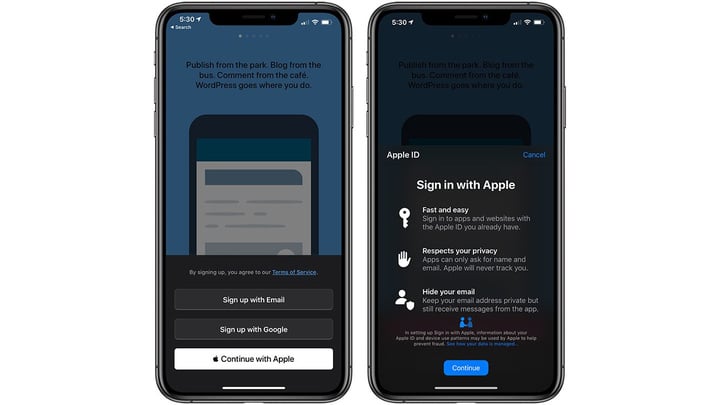
The third-party account logins are often dominated by giants like Facebook and Goolge. The more applications they use to sign in with their accounts, they can capture more personal data and privacy, for companies like them. Your privacy means direct monetary value.
“Log in as an Apple Account” can register and hide your real mailbox through a virtual mailbox, and each application will generate a different virtual mailbox. Apple is currently working on making it easier for more developers to add this feature.
Find My
In the past, when Apple devices were lost, basically they could only rely on the device GPS and WiFi to determine the location. If the device is turned off, it will officially declare cool. Now Apple has introduced a new form of device discovery, and unified the device and friends in “Find My”.
This set of processes is basically like this. When you purchase a new Apple device and log in to your Apple account, the device will generate a unique key based on your account. This key is generated by a mathematical algorithm and will be used every once in a while. Just exchange with your other devices.

▲ “Find My” function. Image from: Six Colors
The key point is that the device will send a Bluetooth broadcast with a key to the surroundings at a certain interval, and the Apple devices around the world can receive the Bluetooth broadcast with the key and upload the key and location information. To Apple (encrypted, Apple can’t see your location).
After Apple’s server there will be a dedicated area to store this information, and when your device loses a request to Apple, Apple will compare the key information to confirm that the user’s lost device belongs to Which user is in what position.

▲ Image from: 9to5mac
The most amazing thing about this technology is that it is a “many and powerful” technology, similar to P2P, the faster the speed, the whole worldWhen there are enough devices in the world, the possibility that the Bluetooth broadcast of the lost device is captured by the surrounding Apple products is higher.
And Apple also uses encryption to ensure the uniqueness and security of the key, and neither the uploader nor Apple knows who is uploading the information. The only thing that can see the location is the loser. .
Safari
Now, Safari has intelligent anti-tracking capabilities in addition to minimizing data delivered to third parties. For example, some social gadgets hidden in the Like, Share, and Comment buttons on social networking sites may track you if you are not using them, and these will now be blocked by Safari. Including the tripartite tracking of cookies and other site data and advertising to you across sites will also be protected by machine-based smart anti-tracking.

▲ Image from: iOS Gadget Hacks
In addition, some websites and advertisers will use your browser configuration, fonts and plug-ins to generate your feature “fingerprint” to personally track and identify you, and Safari will resist this behavior. Provide a simplified version of the system configuration, which will become indiscriminate in the advertiser to prevent tracking behavior.
Other major privacy feature updates include:
- When sharing photos with friends or apps, you can control which information will be shared via menu options (location, edit history, depth of field data, etc.)
- Let you learn through machine learningPeople’s image will not be exposed and shared
- The noise analysis of Apple Watch is analyzed locally on the device and will not be recorded and uploaded to the cloud
- Siri will learn what you need, but Siri won’t know who you are, there will be a random identity when interacting with Siri, and users can now choose whether their data will be uploaded.
- Apple News also generates personalized association services based on random identity
- The wallet and Apple Card number are hidden
- Apple Card purchase information is saved locally, and cannot be seen by anyone other than banks, businesses, and yourself
- The health function saves your health information such as the menstrual cycle, but you can control which data can be added to “health” or share it with others after verification through double verification and biometrics
What is Apple’s Privacy and Security Principles
For Apple, the emphasis on privacy and security has long been a long-term idea, but has been implemented and implemented for many years. Last year’s Cambridge Analytica privacy incident scandal, this year the voice assistants collectively exposed the leak. Apple is the fastest response, and the improvement measures are also the fastest. And iOS 13.2 has further tightened application permissions and implemented more user privacy protections.
Tim Cook said in an interview with Vice News Tonight that privacy issues are already “one of the most important issues of the 21st century,” he added. “When the free market cannot When society brings a good result, you need to ask yourself what you can do. We have to find a new way to reach a new height. We are designing products that are self-challenging to reduce data collection. We encourage ourselves not to go. Identify the content. We won’t look at your email, your information, the user is not our product. And these are not the business we are going to operate.”

▲ Image from: Business Insider
Cook’s words are a good testament to this. On Monday’s privacy-sharing event, Apple engineers shared with us how Apple’s privacy security principles are:
- Try to reduce data from users
- Try to process and save data locally on your device
- Try to be transparent when collecting data
- Run the collected data on a secure platform
When the entire technology industry is seen as a “free” monster that is greedy and hungry and devours user data, when Facebook and Google are seen as the public image of the technology industry. Only Apple, a business model based on the physical product itself, has the ambition to say “privacy protection.” The high price you paid for the iPhone and Mac in the past has become a rare and invisible defense of this era.
The title map source: Malwarebytes Labs