Monitoring and being monitored, this is a big problem
Editor’s note: This article comes from WeChat public account “Brain polar body” (ID : unity007) , author: sea monster.
Applying a quote from Zweig’s “Beheaded Queen”: she was too young at the time to know all the gifts given by fate, and she had already secretly marked the price.
For those who are deeply harmed by spyware, you can put it another way: they were too young at the time, and they did not know that their mobile phone system had been secretly installed with surveillance.
The spyware to be discussed here is mainly an application for monitoring and collecting privacy information for mobile devices such as mobile phones. For many people, the topic of spyware may be new but very sensitive. The strangeness is that we do rarely see such things; the sensitivity lies in the fact that this issue is closely related to us. Because the root of the problem comes from a common life problem-have you ever thought about peeking at a child’s or partner’s phone? Or has your phone been seen by others?
Mobile phones have become the main place of privacy for people. Rather than secretly opening someone else’s mobile phone to see his chat history, it is far more tempting to install a spyware that can get all the information silently.
There are also two scenarios for using this type of spyware: The first type is the most typical, which is monitoring installed by parents to monitor their children’s online behavior. Because of the complex relationship between guardianship and the protection of minors’ privacy, this type of industry is in a relatively sensitive gray area. Another type of surveillance is the unscrupulous monitoring of adults, such as secret monitoring between partners and colleagues, not to mention commercial competition, which clearly belongs to the black industry with illegal activities.
Therefore, this kind of gray-black industrial spyware is being reviewed and banned from the Android iOS system and mobile security software. For those who use these monitoring software, this thing naturally becomes a thing that cannot be said on the table.
But we can’t help but say that because the need for privacy monitoring will always exist, and this type of monitoring software is also flooding, it is impossible not to turn a blind eye to this “elephant in the room”. Recently, the case of KidsGuard, a spyware that inadvertently caused “monitoring data leakage”, became a good opportunity for us to seriously discuss this spyware industry and privacy and security issues.
Spyware who fought with us in those years
Spyware is a concept that appeared in the days when PCs became popular. In 2005, the Anti-Spyware Alliance (ASC) drafted the definition of “spyware”, which weakens users’ ability to control their experience, privacy, and system security.; Use users ‘system resources, including programs installed on their computers; or collect, use, and disseminate users’ personal or sensitive information.
Spyware in a broad sense is a rich gray space, not only involving a lot of adware, pornographic software, and some risky software containing Trojan horse programs. Its main feature is to induce users to install in the system without the user’s permission or in a way that mimics the system software in a false manner.
Think back then, we were always fighting against various spyware. Including small software and plug-ins recommended for new software installation, family buckets pre-made by security software, advertising pop-ups that cannot be closed in the browser, and so on.
This situation has become more hidden and urgent in the era of mobile terminals. Of course, it is more serious in the free and unrestrained Android ecosystem. Due to the early competition between the dazzling Android app store and third-party application market, a large amount of malicious phishing software and spyware induced users to install in their mobile phones, causing various problems such as information leakage, malicious chargeback, and occupation of mobile phone memory.
Even though the regular app store has become the first choice for people to download apps, some spyware still tries to avoid censorship in the app store and mix it into regular software. In early 2018, Google removed 22 malicious adware applications, from flashlights, call recorders to WiFi signal boosters, which have been downloaded 7.5 million times from the Google Play market. At the beginning of last year, an Android-side spyware called MobSTSPY still entered the Google Store and successfully disguised in several applications. It was widely spread around the world using Trojan horse programs to steal user privacy and even phish to collect user account password information. Wait.
Facing increasingly stringent app store censorship and security software protection, spyware is also struggling to survive and change tracks. Mobile phone monitoring software in a legal but gray area has become a new way out. They no longer directly steal user information in the form of hacking to make money from it, but instead provide mobile phone monitoring solutions in the name of protecting children, allowing customers to pay for purchases to obtain revenue. They simply pass the installation task along with the risk of privacy violations to users who place orders. So are these mobile monitoring software easy to use?
Monitoring Waterloo: Who besides you, is watching your child’s phone?
First of all, it can be said responsibly that this kind of software technology is powerful, and it is very easy to use without any trace.
The spyware in question is a child monitoring software called KidsGuard. Recently, data from a cloud server of this software was leaked due to human error, which caused a large amount of data on the monitored devices to be openly exposed to the Internet, which directly caused public panic and worry about this spyware.
Made by KidsGuardAccording to the official website of the manufacturer ClevGuard, this software can “access” all information on the target device, including real-time location, text messages, browser history, photos, videos and application activities, chat screenshots, and phone recordings, etc., almost covering our use of mobile phones All privacy practices.
Through the official shared strategy, we can see how the ClevGuard engineers patiently and meticulously teach you how to break through the Android phone of the target person, and install the KidsGuard software in a few minutes. Even, they also did a ranking of the 8 best Android undetectable spyware in 2020, putting KidsGuard first.
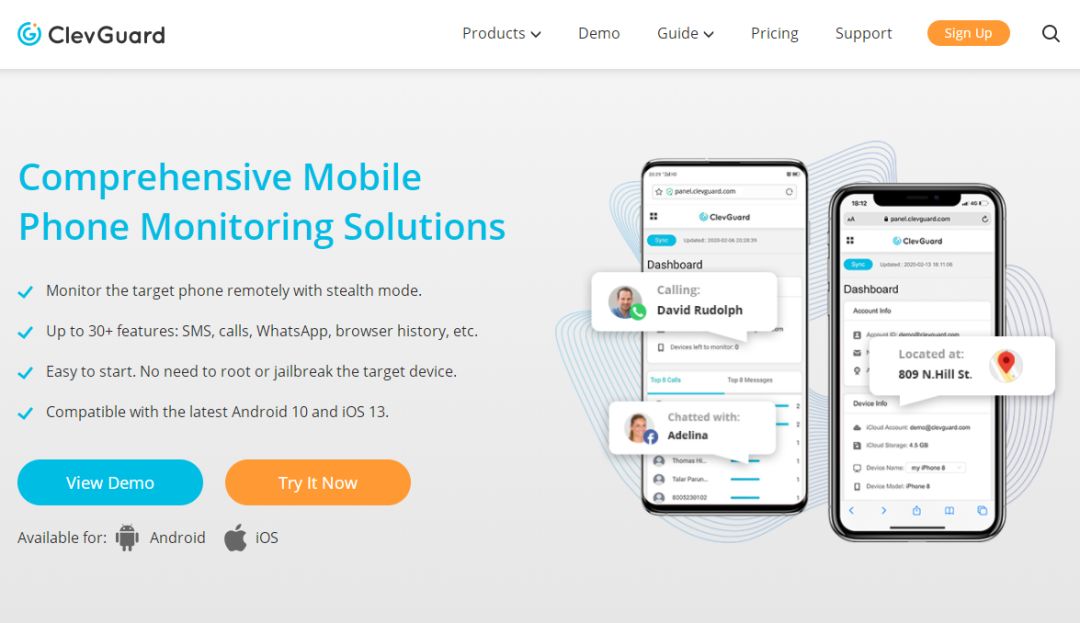
This software claims that it is a “secret” way to protect your children. But they are also publicly publicizing and can be used for other needs, such as grabbing an unfaithful spouse or supervising employees’ mobile phones.
It is reported that the entire installation process will not take more than 1 minute if done skillfully. We will not introduce specific tutorials. At present, at least tens of thousands of mobile phones worldwide are built with this monitoring software. In order to prevent the monitored persons from identifying, they will highly imitate the appearance of Android’s own system and lurk in the mobile phone. The service is really considerate and considerate.
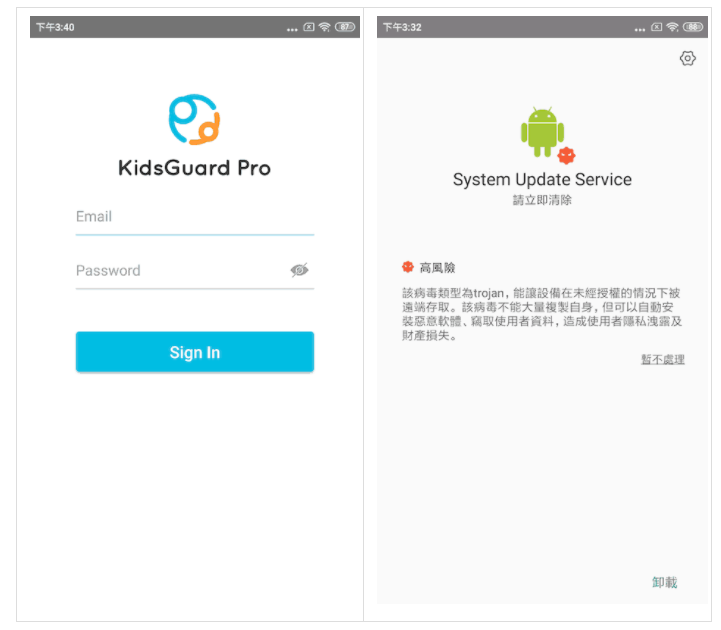
Thinking about these features and usage scenarios is scary. Now, because of what they claim to be “a very serious focus on data privacy and data encryption protection,” there have been major flaws, and this software called “Protecting Vulnerable Children” has gone to its opposite side—exposing user privacy to the public. This result is estimated to be difficult for customers who spend money to use it. It may be a little awkward for some parents to explain this situation to the monitored children, but some customers who monitor adults may also bear the risk of corresponding legal proceedings. .
So what do those people who spend money on monitoring services think?
From gray to black production: uncontrollable mobile monitoring
Spyware monitored by this type of mobile phone”And” black “zones.
In terms of “gray”, KidsGuard’s main positioning is to protect children, that is, to prevent children from being harmed by content such as cyberbullying and pornographic information. Its largest customer base is parents who worry about their children being harmed by illegal information.
This kind of situation involves how to balance the conflict between the parent’s exercise of child custody and the child’s personal privacy protection.
For young children, generally there is no separate Internet device. They usually use their parents’ phones or tablets to surf the Internet and play games. In response to this situation, relevant national regulatory agencies have introduced various online entertainment game platforms that must develop anti-addiction systems and parental control models to ensure that under parental supervision, such parental protection functions can be set up for minors.
For children who already have their own mobile terminal, the situation becomes slightly more complicated. For one thing, it is impossible for parents to stare at their children’s online gaming activities all the time, and for another, children can easily bypass the standardized monitoring settings. The ubiquitous pornographic information from the Internet, the crazy money-drawing games and the bullying and violence information from social networks are indeed very serious “growth troubles” for adolescent children. If there is no good communication, and the children have already attached great importance to their privacy protection, it is difficult for the parents to obtain the health of the online information they pay attention to every day. Faced with these communication difficulties, some parents are naturally inclined to “care” their children through secret surveillance.
But is this desirable? First, the law does not support this behavior by parents. China’s minor protection law provides that “no organization or individual may disclose the privacy of minors.” Whether it is a monitoring platform or parents, in fact, they have been tempted on the verge of violating the law. It depends more on whether the child will sue the parents and let them bear the corresponding legal responsibilities after they know.
And this gray will gradually “deepen”-the monitoring of spouses, partners and even colleagues and subordinates by adults must step out of the legal boundary, which is a naked illegal act. For this type of monitoring software, the publicity of such functions under the cover of child protection has also been an obvious “gray production” economy. For customers who purchase this service, it is also equivalent to blatantly illegal information theft. Such acts urgently need to be punished and sanctioned by relevant laws.
The real “black” is that because spyware itself is on the edge of compliance, there are a large number of spyware that choose to bypass the app store’s audit and install it in users’ phones in various ways. These softwares are not enough in data protection technology. Taking this data breach as an example, a simple reason may cause a large number of data privacy breaches, which is equivalent to exposing thousands of citizens’ big data to the Internet, resulting in Harsh security hazards. Even after bypassing the audit, perhaps a lot of software itself is stealing software under the guise of surveillance. Such asSince then, spyware has become completely black.
From gray to black, we should recognize that there is a real need for mobile monitoring software, and some of the needs are reasonable. But the realization process often goes uncontrollably to darkness.
Trade-off and balance: Protect children properly, is it possible?
On the one hand, this type of monitoring software technology is mature and widely used; on the other hand, parents have a long-standing need for their children’s mobile phone information security. How to choose between actual needs and legal risks? How to balance monitoring technology and information leakage risks? These are still issues that we must face.
We do not need to discuss this type of illegal surveillance by adults. The protection of children’s mobile phone information security is indeed worthy of careful distinction. The core question for mobile monitoring of minors is whether parents should install such mobile monitoring software with their children’s consent.
Obviously, in the ideal situation, parents and children usually have enough communication and understanding to avoid worrying about their children’s online game behavior. Take a step back. Once parents find out that their children have excessive addiction to games or have abnormal information browsing records, parents should take the initiative to communicate with their children, whether they can propose mobile monitoring, limit game time, or limit the use of certain apps or websites. And if the child obviously resists the parent’s monitoring requirements, we recommend that the parents stop this behavior, and even less recommend that the monitoring software be installed silently without the child’s knowledge.
For parents, the child’s problem is not a technical issue, but a long-term emotional investment and equal communication. So what are the warnings of mobile phone monitoring requirements for such security software products in China?
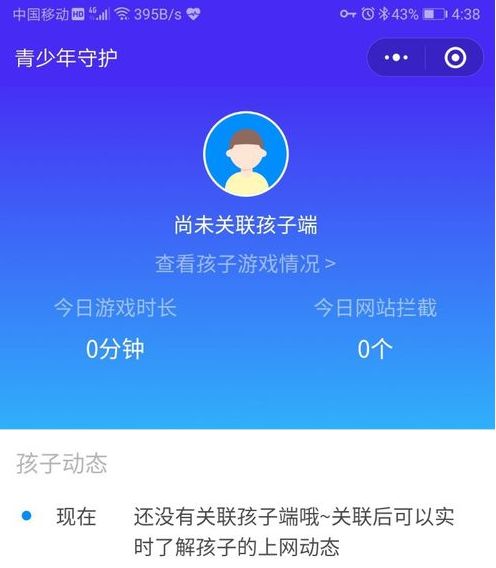
At present, China does not have a completely legal “mobile phone monitoring software”, but there is no clear legislation prohibiting the use of such software. A social communication software in China also launched a corresponding “teenage guardian” program, which can be associated with a child’s mobile phone terminal to obtain dynamic data on its Internet access and games. Its characteristic is that it needs to download the corresponding security protection client in the mobile phone of the minor and set the corresponding permission. Therefore, the monitored person has the right to know to a certain extent, and for children skilled in using mobile phones, this type of monitoring authority can be easily turned off.
For this kind of security software that wants to implement mobile phone monitoring functions, there are two directions that need to be worked on. One is to monitor the protection of private data and prevent the huge information security risk caused by information leakage.One is the design of a more humanized monitoring authority, which can give parents and children more flexible and feasible monitoring solutions to ensure the children’s right to know and choose. At the same time, relevant regulatory agencies and application stores should also strengthen the review of the monitoring functions of such security software.
After all, in the face of children who are easy to let themselves go, fathers and mothers have broken their hearts. Can mobile monitoring be done, or not, and how? Every action and decision matters, and all parties need to think carefully.


On the one hand, this type of monitoring software technology is mature and widely used; on the other hand, parents have a long-standing need for their children’s mobile phone information security. How to choose between actual needs and legal risks? How to balance monitoring technology and information leakage risks? These are still issues that we must face.
We do not need to discuss this type of illegal surveillance by adults. The protection of children’s mobile phone information security is indeed worthy of careful distinction. The core question for mobile monitoring of minors is whether parents should install such mobile monitoring software with their children’s consent.
Obviously, in the ideal situation, parents and children usually have enough communication and understanding to avoid worrying about their children’s online game behavior. Take a step back. Once parents find out that their children have excessive addiction to games or have abnormal information browsing records, parents should take the initiative to communicate with their children, whether they can propose mobile monitoring, limit game time, or limit the use of certain apps or websites. And if the child obviously resists the parent’s monitoring requirements, we recommend that the parents stop this behavior, and even less recommend that the monitoring software be installed silently without the child’s knowledge.
For parents, the child’s problem is not a technical issue, but a long-term emotional investment and equal communication. So what are the warnings of mobile phone monitoring requirements for such security software products in China?

At present, China does not have a completely legal “mobile phone monitoring software”, but there is no clear legislation prohibiting the use of such software. A social communication software in China also launched a corresponding “teenage guardian” program, which can be associated with a child’s mobile phone terminal to obtain dynamic data on its Internet access and games. Its characteristic is that it needs to download the corresponding security protection client in the mobile phone of the minor and set the corresponding permission. Therefore, the monitored person has the right to know to a certain extent, and for children skilled in using mobile phones, this type of monitoring authority can be easily turned off.
For this kind of security software that wants to implement mobile phone monitoring functions, there are two directions that need to be worked on. One is to monitor the protection of private data and prevent the huge information security risk caused by information leakage.One is the design of a more humanized monitoring authority, which can give parents and children more flexible and feasible monitoring solutions to ensure the children’s right to know and choose. At the same time, relevant regulatory agencies and application stores should also strengthen the review of the monitoring functions of such security software.
After all, in the face of children who are easy to let themselves go, fathers and mothers have broken their hearts. Can mobile monitoring be done, or not, and how? Every action and decision matters, and all parties need to think carefully.