It’s really unpredictable.
Editor’s note: This article comes from the WeChat public account ” Suning Financial Research Institute “(ID: SIF-2015) , author Liu Peibin.

You are only allowed to choose one item to go out every day, what would you choose?
I believe everyone has an answer in their hearts, and that is the mobile phone.
Have your work life been filled with mobile phones? Get up in the morning to check the weather, and the mobile app automatically reminds you to pay attention to sun protection; when driving through a certain city, the mobile app immediately recommends clothing, food, housing and transportation in the relevant city. As a senior mobile phone controller, we fully enjoy the convenience brought by various apps.
In addition, whether your mobile phone frequently receives a bunch of spam text messages for preferential activities; in addition to the courier brother calling you, more often the other party directly reports your name, when you think it is an old friend or colleague, But I found that the other party asked you to bring a child to participate in the course experience, or there are discounts for certain houses. Do you hate the disclosure of personal privacy?
Do you understand your phone more and more?
At the end of this article, how malicious apps steal your privacy and teach you how to prevent it.
Privacy leaks are forbidden repeatedly, and precise frauds are frequent
On May 15, 2020, the Ministry of Industry and Information Technology issued an APP notification (the first batch of 2020) on violations of user rights and interests. According to the “Network Security Law”, “Telecommunications Regulations” “Telecommunications and InternetThe Regulations on the Protection of User’s Personal Information “and other laws and regulations, the Ministry of Industry and Information Technology recently organized a third-party testing agency to check mobile phone application software, and supervised and rectified enterprises that found problems.
What apps are there? What violations are they involved in?
According to reports, 16 apps such as Dangdang, store manager direct hire, e-drive, and Dajie are listed. These applications all involve the private collection of personal information. In addition, they also include private sharing with third parties and excessive collection of personal information. 7 types of problems, such as not giving permission and not using it, forcing users to use directional push, excessively requesting permissions, and difficult account cancellation.
Ministry of Industry and Information Technology requires that APPs with problems should complete the implementation of rectification by May 25. If the rectification is not completed within the time limit, the Ministry of Industry and Information Technology will organize relevant disposal work in accordance with laws and regulations.
In August 2018, the China Consumers Association released the “APP Personal Information Leakage Investigation Report”, saying that APP has become a severely affected area for personal information leakage. The number of people who have encountered personal information leakage accounts for 85.2%. The proportion of people who have been to personal information leakage is 14.8%.
When consumers ’personal information was leaked, about 86.5% of the respondents had received harassment from sales calls or text messages, about 75.0% of the respondents had received fraudulent calls, and about 63.4% of the respondents had received spam Mail, ranking in the top three.
The survey results also show that if the mobile APP causes personal information to be leaked, the most worried issue is that it is used to engage in fraud and theft activities, accounting for 70.5%; followed by selling or exchanging to third parties accounting for about 52.4%; being promoted by advertising harassment The ratio is about 37.7%; reputation damage accounts for about 6.6%.
It is worth noting that in the end, about one-third of the respondents chose to “recognize bad luck”, on the one hand, it may be based on the choice of inability to respond, on the other hand, it may also be the response to the status quo of acceptance after invalidity.
After scammers obtain user information, the most worrying thing is to carry out “tailor-made” precise scams on individuals. This kind of scam is difficult to be seen by the parties, because scammers can often accurately say some more private information of the parties. “To be false” is to let users relax their vigilance.
On September 20, 2019, a lady from Shuangyashan, Heilongjiang reported to the police that she had purchased an airplane ticket on a third-party platform a few days ago. Just the day before the plane took off, she suddenly received a text message saying the itinerary cancel. She contacted the phone for a refund and was cheated at 15,000 yuan.
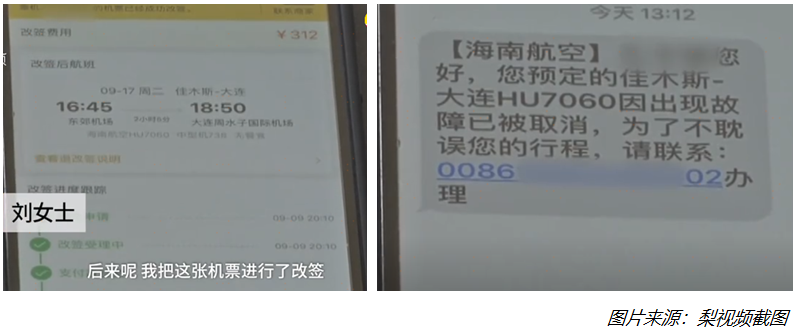
Privacy leaks are diverse, and it ’s difficult to identify routines
There are various reasons for the leakage of personal privacy of users. This section mainly analyzes from four aspects: black and gray personnel, APP developers, APP itself and users themselves.
1. Black and gray personnel steal data by decompiling the system, attacking tampering, implanting backdoors, etc.
In October 2013, the domestic security vulnerability monitoring platform “Wuyun.com” disclosed that a certain company in Zhejiang, which claimed to be China’s largest hotel digital room service provider, had opened a large number of hotels with which it had a cooperative relationship due to a security vulnerability Records leaked online.
A few days later, a file named “2000w open house data” appeared on the Internet, which contained 20 million pieces of personal information about the open house in the hotel, with a capacity of 1.7G. In the opening data, the opening time is from the second half of 2010 to the first half of 2013, including name, gender, nationality, ethnicity, ID number, birthday, address, zip code, mobile phone, fixed line, fax, email, company, accommodation time 14 fields.
Hackers use platform vulnerabilities to collect personal information leaked from websites and APP applications, and then try to log in to other website systems to “crash the library” to continuously obtain user information illegally. Through the mobile phone number and ID number, the user’s fragmentation information is continuously correlated and cleaned, and then the information is “packaged” and sold to criminals in order to profit.
At present, “human flesh search” has become a gray business, with prices ranging from several hundred yuan to several thousand yuan, and these information come from the “social work library” used by black and gray people to store personal information.
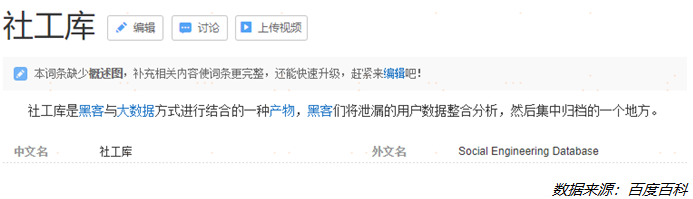
It should be noted that the social work library and the “human flesh search” behavior seriously violated the provisions of the “Internet Security Law” and other relevant laws and administrative regulations on the protection of personal information.
2. The technical strength of APP developers varies, and poor data management can easily lead to data leakage
Generally, APP developers of small and medium-sized companies have weak technical capabilities, lack of data security technical strength, and poor awareness of data protection. This gives hackers the opportunity.
Taking the financial industry APP as an example, how safe are these APPs related to “money”? On September 11, 2019, the report team of China Information and Communications Technology Institute included 232 Android application markets 133327 financial industry apps.
After testing, a total of 20.48% of financial industry apps have been embedded with third-party SDKs, and the total number of embedded SDKs is as high as 104005. Among the financial industry apps embedded in the SDK, 45% of the apps have embedded five or more SDKs. The third-party SDK has hidden security risks such as the collection of user information and its own security vulnerabilities that are easily used by criminals.
Only 17.08% of these batches of apps have undergone security hardening, and more than 80% of financial industry apps have “streaking” in the application market without any security hardening. If Android applications written based on the Java language are not hardened, the packaged APK files can easily be reversely analyzed by the decompilation tool, thereby exposing risks.
3. The APP itself excessively asks for mobile phone permissions to bring privacy risks
For APP, part of the access to mobile phone permissions is due to functional requirements (such as navigation software to obtain location information); on the other hand, it is also to collect as much user data as possible, understand user characteristics in more detail, and then target To promote and improve user experience.
What APP is most keen to collect is to obtain user location and address book information. According to the “APP Personal Information Leakage Investigation Report”, the right to read location information and access to contacts are the most encountered when installing and using mobile apps, accounting for 86.8% and 62.3%, respectively. Respondents were also asked to read call record permissions (47.5%), read SMS record permissions (39.3%), open camera permissions (39.3%), and microphone recording permissions (24.6%).
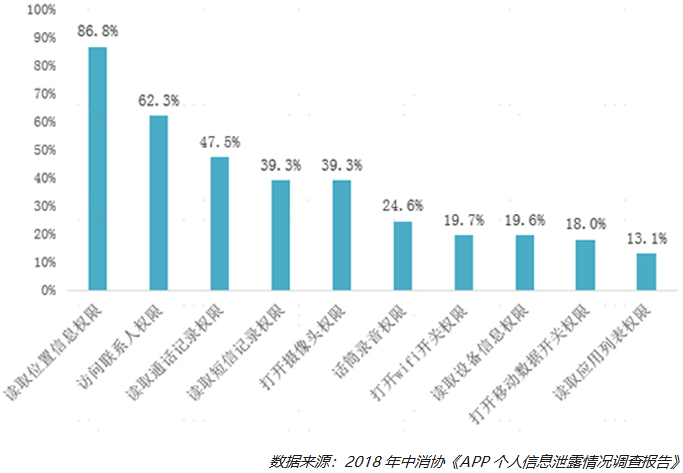
When the APP is installed, there is a service agreement and privacy policy, which is several pages or even dozens of pages and the text is intensive. Some software cannot be used without authorization, and most users are not interested in reading and directly choose to agree by default. Some seemingly “regular” APPs have buried traps within the terms, dressed in “legal” cloaks, and collected user personal information on the grounds of “I have read and agreed to perform”. When he was found to protect his rights, he excused himself on the grounds that “the requirements have been stated in the clauses and the user has agreed”.
4. The user ’s own lack of security awareness, which ca n’t stand the “temptation” can easily lead to privacy leakage
In the Internet era, a large number of users do not know how to manage it properlyManage account passwords, generally lack of security awareness, easy to be poisoned or deceived by phishing software.
A large number of high-quality imitation and low-quality apps are flooding the market. Taking IOS Appstore search for “Check Social Security” as an example, dozens of similar apps come out. It is difficult for ordinary users to distinguish which one is officially produced. The top-ranked apps may be washed up by means of reviews, downloads, etc. of. In the process of user registration, their data is retained by these apps.
In 315 in 2019, “Social Security Handbook” was named because of excessive collection of user information data. After users fill in various materials to register this APP, this APP will steal user social security information through hidden user terms. Has been removed from the entire network.
Some apps also attract users to download apps directly through tempting information such as preferential SMS links and scan codes. At this time, the user should keep his eyes clear, do not make it convenient or just look at the evaluation, etc., do not download and enter personal information when the source of the APP is not clear. When using certain functions of the APP to prompt the need to read the address book, you must carefully consider whether this requirement is reasonable and increase your own discriminating ability and privacy protection awareness.
Passion for personal privacy, business interests are the incentives
The essence of business is profit-seeking, and it is understandable to use data correctly and reasonably. As Baidu CEO Li Yanhong said, in most cases, Chinese people are willing to use privacy for convenience, but users still do not want to be over-checked on their personal data, such as chat history and call history.
Aside from illegal activities such as “selling and exchanging personal information” and “fraudulent activities,” how is personal information used to promote advertising? Let you understand the advertising, this section briefly introduces the routines for you.
First of all, when we register to use the shopping or social APP, your name, mobile phone number, gender and address will be recorded.
Secondly, when you use the APP, your behavior data such as browsing time, geographic location, browsing path, consumption records, etc. will be saved.
Next, the system builds a model, builds tags from these basic data and behavior data, and tries to build your user portrait from countless tags.
For example, you see an introduction to a “TV” product, and the system calculates how much you want to buy “TV”. Through a simple label weighting algorithm:
Purchase desire weight = behavior weight × residence time × decay factor
When you perform reviews, likes, reposts and favorites on TV products, your behavior weight will increase. Stay time is a plus point. If you browse the “TV” for a long time, you are interested in it. A short stay cannot represent you longDuring the period of interest, the weight of a single browsing behavior will continue to decay over time.
Finally, based on these tags, the system recommends products to you through your browsing behavior; you can also recommend browsing records and purchased products of other users similar to you.
In the early days of the Internet, “The New Yorker” once had a globally famous slang: “On the Internet, no one knows that you are a dog.” Now, dogs know you better than you.
Prevent privacy leakage and enhance personal security awareness
How to protect our personal privacy in the Internet age? It requires the joint efforts of APP developers, application distribution markets and APP users.
1, APP developers fulfill their responsibilities and protect personal privacy from the source
An APP goes online, and it has to go through the design, development and go-live process. App developers need to consciously abide by the relevant laws such as “Approval Methods for Collecting and Using Personal Information of APPs”, and follow the basic principles of personal data collection, including clear purpose, minimum use, public notification, and personal consent. Establish a so-called “accountability system” for information leaks, so that everyone can pay more attention to the solution of data problems.
2. The application distribution platform improves the review mechanism to help users keep the “last door”
The number of domestic app stores in China has exceeded 200. Most app stores have introduced certain measures to ensure users ’safety experience. It is particularly important to strictly audit and check to improve the user experience. Some application distribution platforms have adopted a four-fold detection system of “malicious behavior detection” + “privacy leak detection” + “security vulnerability scanning” + “manual real-name review” to ensure the safety and compliance of the listed applications with various security audit measures.
3. APP users strengthen their awareness of information security protection and prevent illegal applications from taking advantage of “organic opportunities”
APP users can specifically strengthen the security of personal information through the following four methods:
(1) Manage the APP in different levels and set different account passwords. For APPs involving funds and general APPs, setting two different sets of accounts and passwords can prevent serial number theft.
(2) Do not log in free WiFi at will, and swipe the QR code at will. When downloading the APP, it is best to download it from the official website, or through the third-party application market of qualified operation, and properly check the qualification of the publisher. Copycat apps, or apps that have problems such as stealing personal information and malicious deductions, should be identified in advance to prevent them from falling into the copycat trap.
(3) Turn off the sensitive right of APPlimit. Check the permissions requested by the application, and close sensitive permissions such as reading the address book and reading SMS call records.
For Apple phones, click Settings-Privacy to see which programs are still using your “location services”, “address book” and other services. Turn off Settings-General-Background application refresh function, some apps collect user information through the background application refresh function.
For Android phones, carefully turn on the USB debugging mode, because once the mobile phone is turned on the USB debugging mode, the PC software can quickly root the phone. Once you have root permissions, the information such as the lock screen password and account binding of the phone can be easily called by other software, and its security risks are self-evident.
(4) Do not fill in personal information at will, and do not disclose it actively. Usually receive express delivery, use Mr./Ms. X, preferential use of community self-lifting cabinet, do not correspond to specific house number; use privacy trumpet for contact, etc.

There are various reasons for the leakage of personal privacy of users. This section mainly analyzes from four aspects: black and gray personnel, APP developers, APP itself and users themselves.
1. Black and gray personnel steal data by decompiling the system, attacking tampering, implanting backdoors, etc.
In October 2013, the domestic security vulnerability monitoring platform “Wuyun.com” disclosed that a certain company in Zhejiang, which claimed to be China’s largest hotel digital room service provider, had opened a large number of hotels with which it had a cooperative relationship due to a security vulnerability Records leaked online.
A few days later, a file named “2000w open house data” appeared on the Internet, which contained 20 million pieces of personal information about the open house in the hotel, with a capacity of 1.7G. In the opening data, the opening time is from the second half of 2010 to the first half of 2013, including name, gender, nationality, ethnicity, ID number, birthday, address, zip code, mobile phone, fixed line, fax, email, company, accommodation time 14 fields.
Hackers use platform vulnerabilities to collect personal information leaked from websites and APP applications, and then try to log in to other website systems to “crash the library” to continuously obtain user information illegally. Through the mobile phone number and ID number, the user’s fragmentation information is continuously correlated and cleaned, and then the information is “packaged” and sold to criminals in order to profit.
At present, “human flesh search” has become a gray business, with prices ranging from several hundred yuan to several thousand yuan, and these information come from the “social work library” used by black and gray people to store personal information.

It should be noted that the social work library and the “human flesh search” behavior seriously violated the provisions of the “Internet Security Law” and other relevant laws and administrative regulations on the protection of personal information.
2. The technical strength of APP developers varies, and poor data management can easily lead to data leakage
Generally, APP developers of small and medium-sized companies have weak technical capabilities, lack of data security technical strength, and poor awareness of data protection. This gives hackers the opportunity.
Taking the financial industry APP as an example, how safe are these APPs related to “money”? On September 11, 2019, the report team of China Information and Communications Technology Institute included 232 Android application markets 133327 financial industry apps.
After testing, a total of 20.48% of financial industry apps have been embedded with third-party SDKs, and the total number of embedded SDKs is as high as 104005. Among the financial industry apps embedded in the SDK, 45% of the apps have embedded five or more SDKs. The third-party SDK has hidden security risks such as the collection of user information and its own security vulnerabilities that are easily used by criminals.
Only 17.08% of these batches of apps have undergone security hardening, and more than 80% of financial industry apps have “streaking” in the application market without any security hardening. If Android applications written based on the Java language are not hardened, the packaged APK files can easily be reversely analyzed by the decompilation tool, thereby exposing risks.
3. The APP itself excessively asks for mobile phone permissions to bring privacy risks
For APP, part of the access to mobile phone permissions is due to functional requirements (such as navigation software to obtain location information); on the other hand, it is also to collect as much user data as possible, understand user characteristics in more detail, and then target To promote and improve user experience.
What APP is most keen to collect is to obtain user location and address book information. According to the “APP Personal Information Leakage Investigation Report”, the right to read location information and access to contacts are the most encountered when installing and using mobile apps, accounting for 86.8% and 62.3%, respectively. Respondents were also asked to read call record permissions (47.5%), read SMS record permissions (39.3%), open camera permissions (39.3%), and microphone recording permissions (24.6%).

When the APP is installed, there is a service agreement and privacy policy, which is several pages or even dozens of pages and the text is intensive. Some software cannot be used without authorization, and most users are not interested in reading and directly choose to agree by default. Some seemingly “regular” APPs have buried traps within the terms, dressed in “legal” cloaks, and collected user personal information on the grounds of “I have read and agreed to perform”. When he was found to protect his rights, he excused himself on the grounds that “the requirements have been stated in the clauses and the user has agreed”.
4. The user ’s own lack of security awareness, which ca n’t stand the “temptation” can easily lead to privacy leakage
In the Internet era, a large number of users do not know how to manage it properlyManage account passwords, generally lack of security awareness, easy to be poisoned or deceived by phishing software.
A large number of high-quality imitation and low-quality apps are flooding the market. Taking IOS Appstore search for “Check Social Security” as an example, dozens of similar apps come out. It is difficult for ordinary users to distinguish which one is officially produced. The top-ranked apps may be washed up by means of reviews, downloads, etc. of. In the process of user registration, their data is retained by these apps.
In 315 in 2019, “Social Security Handbook” was named because of excessive collection of user information data. After users fill in various materials to register this APP, this APP will steal user social security information through hidden user terms. Has been removed from the entire network.
Some apps also attract users to download apps directly through tempting information such as preferential SMS links and scan codes. At this time, the user should keep his eyes clear, do not make it convenient or just look at the evaluation, etc., do not download and enter personal information when the source of the APP is not clear. When using certain functions of the APP to prompt the need to read the address book, you must carefully consider whether this requirement is reasonable and increase your own discriminating ability and privacy protection awareness.
Passion for personal privacy, business interests are the incentives
The essence of business is profit-seeking, and it is understandable to use data correctly and reasonably. As Baidu CEO Li Yanhong said, in most cases, Chinese people are willing to use privacy for convenience, but users still do not want to be over-checked on their personal data, such as chat history and call history.
Aside from illegal activities such as “selling and exchanging personal information” and “fraudulent activities,” how is personal information used to promote advertising? Let you understand the advertising, this section briefly introduces the routines for you.
First of all, when we register to use the shopping or social APP, your name, mobile phone number, gender and address will be recorded.
Secondly, when you use the APP, your behavior data such as browsing time, geographic location, browsing path, consumption records, etc. will be saved.
Next, the system builds a model, builds tags from these basic data and behavior data, and tries to build your user portrait from countless tags.
For example, you see an introduction to a “TV” product, and the system calculates how much you want to buy “TV”. Through a simple label weighting algorithm:
Purchase desire weight = behavior weight × residence time × decay factor
When you perform reviews, likes, reposts and favorites on TV products, your behavior weight will increase. Stay time is a plus point. If you browse the “TV” for a long time, you are interested in it. A short stay cannot represent you longDuring the period of interest, the weight of a single browsing behavior will continue to decay over time.
Finally, based on these tags, the system recommends products to you through your browsing behavior; you can also recommend browsing records and purchased products of other users similar to you.
In the early days of the Internet, “The New Yorker” once had a globally famous slang: “On the Internet, no one knows that you are a dog.” Now, dogs know you better than you.
Prevent privacy leakage and enhance personal security awareness
How to protect our personal privacy in the Internet age? It requires the joint efforts of APP developers, application distribution markets and APP users.
1, APP developers fulfill their responsibilities and protect personal privacy from the source
An APP goes online, and it has to go through the design, development and go-live process. App developers need to consciously abide by the relevant laws such as “Approval Methods for Collecting and Using Personal Information of APPs”, and follow the basic principles of personal data collection, including clear purpose, minimum use, public notification, and personal consent. Establish a so-called “accountability system” for information leaks, so that everyone can pay more attention to the solution of data problems.
2. The application distribution platform improves the review mechanism to help users keep the “last door”
The number of domestic app stores in China has exceeded 200. Most app stores have introduced certain measures to ensure users ’safety experience. It is particularly important to strictly audit and check to improve the user experience. Some application distribution platforms have adopted a four-fold detection system of “malicious behavior detection” + “privacy leak detection” + “security vulnerability scanning” + “manual real-name review” to ensure the safety and compliance of the listed applications with various security audit measures.
3. APP users strengthen their awareness of information security protection and prevent illegal applications from taking advantage of “organic opportunities”
APP users can specifically strengthen the security of personal information through the following four methods:
(1) Manage the APP in different levels and set different account passwords. For APPs involving funds and general APPs, setting two different sets of accounts and passwords can prevent serial number theft.
(2) Do not log in free WiFi at will, and swipe the QR code at will. When downloading the APP, it is best to download it from the official website, or through the third-party application market of qualified operation, and properly check the qualification of the publisher. Copycat apps, or apps that have problems such as stealing personal information and malicious deductions, should be identified in advance to prevent them from falling into the copycat trap.
(3) Turn off the sensitive right of APPlimit. Check the permissions requested by the application, and close sensitive permissions such as reading the address book and reading SMS call records.
For Apple phones, click Settings-Privacy to see which programs are still using your “location services”, “address book” and other services. Turn off Settings-General-Background application refresh function, some apps collect user information through the background application refresh function.
For Android phones, carefully turn on the USB debugging mode, because once the mobile phone is turned on the USB debugging mode, the PC software can quickly root the phone. Once you have root permissions, the information such as the lock screen password and account binding of the phone can be easily called by other software, and its security risks are self-evident.
(4) Do not fill in personal information at will, and do not disclose it actively. Usually receive express delivery, use Mr./Ms. X, preferential use of community self-lifting cabinet, do not correspond to specific house number; use privacy trumpet for contact, etc.
How to protect our personal privacy in the Internet age? It requires the joint efforts of APP developers, application distribution markets and APP users.
1, APP developers fulfill their responsibilities and protect personal privacy from the source
An APP goes online, and it has to go through the design, development and go-live process. App developers need to consciously abide by the relevant laws such as “Approval Methods for Collecting and Using Personal Information of APPs”, and follow the basic principles of personal data collection, including clear purpose, minimum use, public notification, and personal consent. Establish a so-called “accountability system” for information leaks, so that everyone can pay more attention to the solution of data problems.
2. The application distribution platform improves the review mechanism to help users keep the “last door”
The number of domestic app stores in China has exceeded 200. Most app stores have introduced certain measures to ensure users ’safety experience. It is particularly important to strictly audit and check to improve the user experience. Some application distribution platforms have adopted a four-fold detection system of “malicious behavior detection” + “privacy leak detection” + “security vulnerability scanning” + “manual real-name review” to ensure the safety and compliance of the listed applications with various security audit measures.
3. APP users strengthen their awareness of information security protection and prevent illegal applications from taking advantage of “organic opportunities”
APP users can specifically strengthen the security of personal information through the following four methods:
(1) Manage the APP in different levels and set different account passwords. For APPs involving funds and general APPs, setting two different sets of accounts and passwords can prevent serial number theft.
(2) Do not log in free WiFi at will, and swipe the QR code at will. When downloading the APP, it is best to download it from the official website, or through the third-party application market of qualified operation, and properly check the qualification of the publisher. Copycat apps, or apps that have problems such as stealing personal information and malicious deductions, should be identified in advance to prevent them from falling into the copycat trap.
(3) Turn off the sensitive right of APPlimit. Check the permissions requested by the application, and close sensitive permissions such as reading the address book and reading SMS call records.
For Apple phones, click Settings-Privacy to see which programs are still using your “location services”, “address book” and other services. Turn off Settings-General-Background application refresh function, some apps collect user information through the background application refresh function.
For Android phones, carefully turn on the USB debugging mode, because once the mobile phone is turned on the USB debugging mode, the PC software can quickly root the phone. Once you have root permissions, the information such as the lock screen password and account binding of the phone can be easily called by other software, and its security risks are self-evident.
(4) Do not fill in personal information at will, and do not disclose it actively. Usually receive express delivery, use Mr./Ms. X, preferential use of community self-lifting cabinet, do not correspond to specific house number; use privacy trumpet for contact, etc.